NIS 2: Developing Cyber Maturity and Compliance through Cyber Risk Quantification (CRQ)

On 18 October 2024, the European NIS 2 (Network and Information Security) Directive must be transposed into national law, affecting many sectors of the European economy. It strengthens the NIS 1 Directive, which was adopted in 2016 and set in motion an institutional and regulatory approach to cybersecurity in the European Union. The aim of the new directive is to bring the 27 Member States up to the same level of maturity when it comes to cybersecurity issues. NIS 1 had enabled many European companies to better protect themselves against cyber-attacks, and the overall impact of this directive had been conclusive. The harmonisation foreseen in NIS 2 aims to extend the scope of cybersecurity regulations to fully protect services and sectors of strategic importance, while introducing a principle of proportionality.
As a result, many businesses not covered by NIS 1 will have to comply by the end of 2024. Like the Digital Operational Resilience Act (DORA), Cyber Risk Quantification (CRQ) will enable businesses to take a strategic, quantified and structured approach to cyber risk management.
NIS 2 : Who has to apply this Directive ?
The NIS 2 Directive extends the scope of the NIS 1 Directive and now applies to new sectors not previously covered by cybersecurity legislation. These sectors are not all subject to the same restrictions, depending on whether they are listed in Annex 1 or Annex 2 of the Directive.
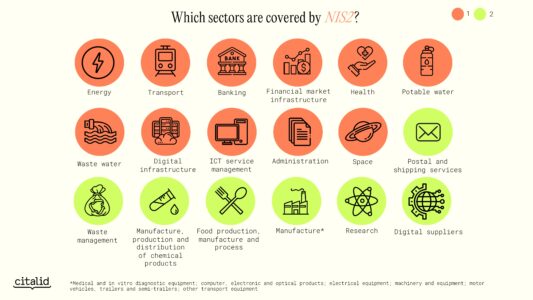
The new Directive distinguishes between two types of entities: essential entities and significant entities. An organisation is a “essential entity” if it is large or medium-sized, has 50 or more employees and a turnover of €20 million or more, and its sector of activity is listed in Annex 1. “Important entities” are :
- Medium-sized entities carrying out activities corresponding to the identity types in Annex 1
- Medium-sized entities and above carrying out activities corresponding to Annex 2.
The NIS 2 Directive applies indirectly to the suppliers and service providers of the entities concerned, as it imposes an obligation to secure the supply chain of essential and important entities. The number of organisations affected is therefore higher than might be expected.
What are the main requirements ?
Companies affected by NIS2 must implement a series of cybersecurity measures. These measures have not yet been specified by the ANSSI, which is responsible for transposing the directive into French law. Based on the directive, organisations will have to think about cyber crisis management, in particular by setting up business continuity plans (BCP), disaster recovery plans (DRP) and backup management plans. The aim is to know how to respond in the event of a cyber attack and to ensure that the impact on the business is minimised. In the event of a crisis, secure communications solutions must be in place.
- The measures introduced by the NIS2 Directive are primarily technical. Organisations will have to adopt specific practices to ensure their own cyber security and that of their staff: use of multi-factor or continuous authentication solutions, policies and procedures on cryptography, policies on risk analysis and PSSI, etc. Great attention will have to be paid to the acquisition, development and maintenance of information networks and services, with a focus on vulnerability management.
- The NIS2 Directive also contains operational measures. Organisations will be required to report cyber security incidents to a specialised body, the Computer Security Incident Response Team (CSIRT). Depending on the severity of the incident, the CSIRT may advise the entity on the procedures to be put in place or alert other Member States. Notification takes place in three stages. First, organisations must make an “initial notification” within 24 hours of the incident. This is followed by a “detailed notification” within 72 hours of the incident. Finally, the organisation must submit a ‘final report’ to the CSIRT the following month. This process not only enables a response to be made, but also documents the management of the crisis.
- Finally, NIS2 provides for organisational measures. It also emphasises the responsibility of the board of directors with regard to cyber security within the company. To be able to take decisions in this area, its members must be trained in cyber risk management, in order to be able to assess the impact on the services provided by the company and the procedures to be put in place. They must also be able to approve and monitor the implementation of measures taken by IT departments. Failure to comply with the NIS2 Directive will expose the board to criminal liability and sanctions. A significant organisation can be fined €10 million or 2% of its annual worldwide turnover. This rises to €7 million or 1.4% of annual worldwide turnover for a large company.
Cyber Risk Quantification (CRQ) is the first step towards compliance
The use of a cyber risk quantification solution, also known as CRQ, is a first step towards compliance with NIS2, particularly in relation to the organisational measures mentioned above.
This approach involves assessing an organisation’s exposure to cyber risk, using financial indicators to inform decisions on risk mitigation or sharing.
The financial quantification of cyber risk establishes a common language between the technical teams responsible for cyber security and the management body. As the latter will be held responsible in the event of an incident or non-compliance with the NIS2 directive, the use of financial data enables a dialogue to take place and the right decisions to be made in terms of risk management.
Combined with a detailed, contextualised understanding of the threat, quantifying cyber risk helps organisations to prioritise appropriate defences and rationalise their security spend. This approach helps to better manage risks and their impact on critical infrastructure. Organisations affected by NIS 2 can therefore align their security measures with the requirements of the European Directive.
One of the objectives of cyber risk quantification solutions is to generate harmonised indicators to estimate the level of risk an organisation is exposed to in financial terms. These metrics are then used to demonstrate compliance efforts to the organisation’s risk management ecosystem: IT teams, management, insurers, regulators, etc.
Cyber risk quantification is based on incident scenarios (or types of attacks) and analyses their estimated financial impact. This approach helps organisations to develop robust incident response plans in line with the NIS 2 Directive. This makes them more resilient and enables them to recover quickly and effectively in the event of an incident.
Finally, the quantification of cyber risk is a method that contributes to the management of risks related to the organisation’s ecosystem (suppliers, customers, partners, etc.), in particular its supply chain, because it is taken into account in the organisation’s environment, the risks of which are quantified. NIS 2 highlights the importance of these risks. This ensures that organisations do not limit their risk management to their internal systems, but also consider the risks associated with their supply chain.
Quantifying cyber risk is not only a way to kick-start compliance, but also to focus efforts on achieving results. It also reflects a new minimalist approach to cyber security. The use of a cyber risk quantification solution is therefore part of a reflection on the ROI of cybersecurity, with the adoption of new practices, of which NIS 2 can be the starting point.
For example, quantifying cyber risk using the Citalid platform provides a better understanding of the financial impact of a successful attack on an organisation, thanks to our expertise in more than 1,000 modelled scenarios.
Citalid: quantifying cyber risk and taking action
The platform developed by Citalid is based on the FAIR (Factor Analysis of Information Risk) methodology. This is based on the principle that cyber risk can be quantified in financial terms by correlating the factors that determine the frequency of attacks and the cost of successful attacks.
It is also enriched by business expertise in Cyber Threat Intelligence (CTI), through the continuous monitoring of more than 700 global cybercrime actors. By adding these elements, the cyber threat is contextualised, allowing a more detailed analysis of the organisation’s exposure, understood in its environment.
Citalid simply and reliably measures the financial risk borne by the organisation in relation to its vulnerabilities and threat context. Among the use cases offered by the Citalid platform, the implementation of a cybersecurity roadmap makes it possible to prioritise and evaluate the security measures taken to reduce risk. Once the risk is under control, and in the context of NIS2, it is possible to focus on other compliance-related tasks: setting up DRP and BCP plans, raising awareness and training staff, etc.
ANSSI encourages organisations affected by NIS 2 to take out insurance against cyber risks. Another use case for the Citalid platform is to gain a better understanding of your residual risk so that you can better assess your coverage and cyber insurance needs. As an insured, you will have factual and measurable elements to discuss with your insurer in order to negotiate and choose the most appropriate insurance policy for each company.
Want to implement a transparent and simple risk quantification solution as part of your NIS 2 or DORA compliance process? Book your demo now.

