BlackCat/ALPHV: A Sophisticated and Prolific Ransomware Operation

At Citalid, we combine strategic Cyber Threat Intelligence (CTI) and predictive algorithms to unlock the power of Cyber Risk Quantification (CRQ). Our CTI team monitors over 700 threat actors in real-time to dynamically fuel our CRQ engines. From this continuous analysis, the team dives into deeper CTI reports and geopolitical context analyses.
In today’s post, Citalid’s Cyber Threat Intelligence team will review BlackCat/ALPHV’s operations and methods.
Blackcat Ransomware: Nature, Genesis, and Beginnings
BlackCat was first observed in November 2021 and operates as a Ransomware-as-a-Service (RaaS). BlackCat employs a double extorsion strategy. Affiliates exfiltrate data before encrypting the compromise system and threaten to publish it to add pressure and maximize the chances of ransom payment. In some cases, triple extorsion were reported. That is, the use of a distributed-denial-of-service to plunge the target into total intertia.
Blackcat’s playload has strong technical overlaps with REvil, Darkside, known for the Colonial Pipeline attacks and Blackmatter. It is still uncertian whether the operation is a rebrand of the latter or the consequence of a member of the team starting a new operation. There is a clear consensus however that the geneses of Blackcat lies with these other groups showing high persistence and versatility of high-profile cybercriminals. Thus, usurpingly, Blackcat’s operators are believed to originate from the Commonwealth of Independent States (CIS).
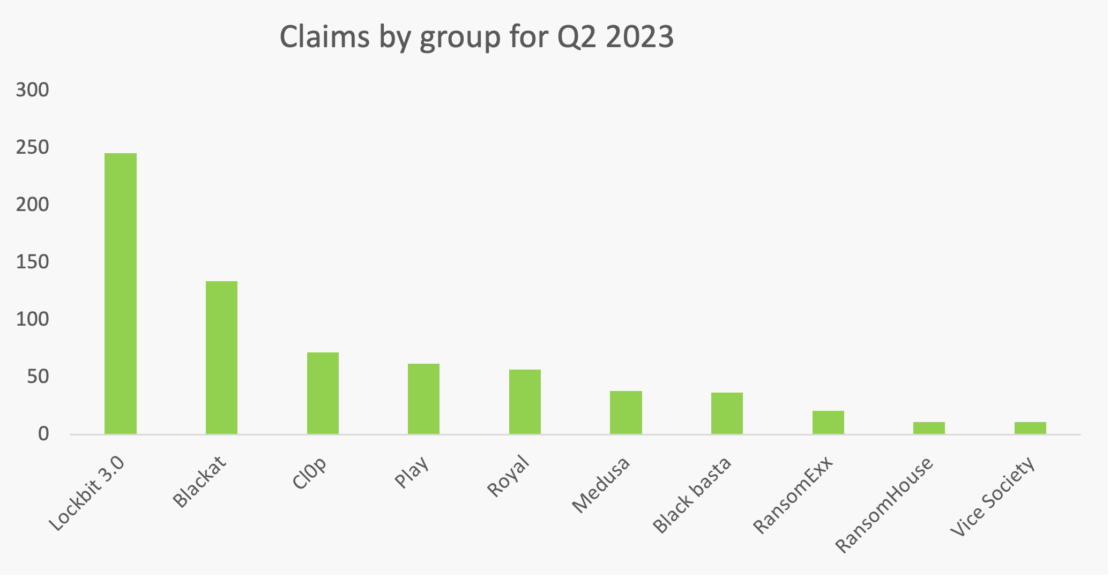
Victimology Over the last quarter Blackcat claimed over 130 victims, an historically high score for the ransomware’s operators compared to 2022 level (60 per quarter on average). While RaaS offering multiplied in recent years giving the cybercriminal ecosystem the semblance of a competitive marketplace, this increase and longevity tends to show Blackcat’s attractiveness to ransomware affiliates. This level of activity makes Blackcat as one of the most prolific ransomware operations currently active.
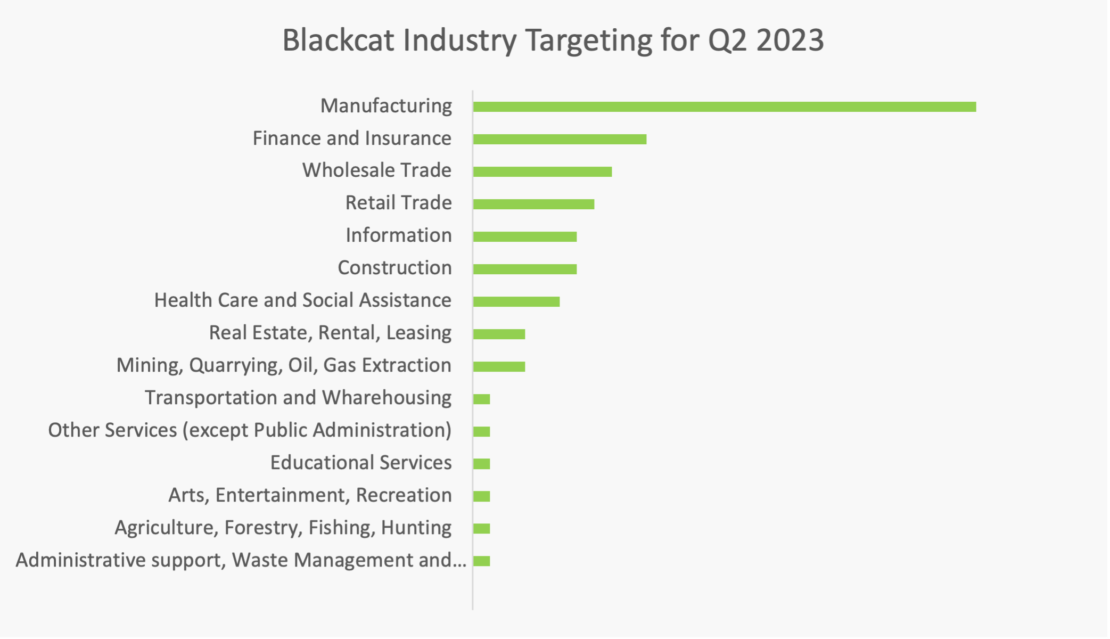
Affiliates primarily focus on seemingly highly solvable targets operating in finance, drug manufacturing and legal services. Blackcat’s affiliates heavily target western countries with a heavy focus of the United-States. Over half of claimed victims are small size companies and medium size companies weight for a third of claimed victims.
Toolkit and Capabilities
Unlike other ransomware groups that typically code in C++, BlackCat is written in Rust, enabling it to compromise information systems running on Windows, Linux, and VMWare ESXI.
Blackcat’s uniqueness and most distinguished factor is the use and development of their own tailored and highly customizable tools. Blackcat toolkit heavily relies on internally developed capabilities, which are regularly updated and reinforced with new features. A JSON configuration file allows affiliates among other things, to use extension, target specific services.
For exfiltration, Blackcat uses Exmatter. Likewise, this part of the toolkit has undergone several development phases mainly to improve detection evasion. Since September 2022, this tool can be used to corrupt files after exfiltration instead of encrypting them. Has said, the ransomware-as-a-service landscape has become highly competitive in recent years. These evolutions demonstrate a high capacity for adaptation, innovation both to secure attack success via a highly sophisticated toolkit with great damaging potential and to optimize costs and stability issues.
Blackcat’s innovation spirit for cyber extorsion is not limited to its technical capabilities. Recent studies show that ransomware victims are increasingly reluctant to pay ransoms. This has largely contributed to the decline in ransomware revenues. Blackcat developed a direct disclosure approach. They have been seen directly contacting customers, business partners, employees or even media organizations to communicate about an attack. More importantly, in June 2022, Blackcat operators opened a leak website on the clear web. This website offers a valuable feature that allows customers or employees of previously compromised companies to check whether their personal data was affected during the attack. Moreover, it benefits from effective referencing, making the disclosed data easily accessible.
Blackcat’s Techniques, Tactics and Procedures
| Tactic | Technique |
| Initial Access | T1078 : Valid Accounts |
| Execution | T1059.003 : Command and Scripting Interpreter : Windows Command Shell |
| T1047 : Windows Management Instrumentation | |
| Credential Access | T1528 : Steal Application Access Token |
| T1558 : Steal or Forge Kerberos Tickets | |
| Privilege Escalation | T1548.002 : Abuse Elevation Control Mechanism : Bypass User Account Control |
| T1134 : Access Token Manipulation | |
| Defense Evasion | T1548.002 : Abuse Elevation Control Mechanism : Bypass User Account Control |
| T1070.001 : Clear Windows Event Logs | |
| T1222.001 : File and Directory Permissions Modification : Windows File and Directory Permissions Modification | |
| T1112 : Modify Registry | |
| T1134 : Access Token Manipulation | |
| Discovery
| T1087.002 : Account Discovery : Domain Account |
| T1083 : File and Directory Discovery | |
| T1135 : Network Share Discovery | |
| T1069.002 : Permission Groups Discovery : Domain Groups | |
| T1018 : Remote System Discovery | |
| T1082 : System Information Discovery | |
| T1033 : System Owner / User Discovery | |
| Lateral Movement | T1570 : Lateral Tool Transfer |
| Persistence | T1098 : Account Manipulation |
| T1133 : External Remote Services | |
| Impact | T1486 : Data Encrypted For Impact |
| T1491.001 : Defacement : Internal Defacement | |
| T1561.001 : Disk Wipe : Disk Content Wipe | |
| T1490 : Inhibit System Recovery | |
| T1489 : Service Stop |
We hope this analysis was able to enlighten your knowledge on Blackcat/ALPHV and by extension on the methodology of such advanced ransomware operation. We strongly believe that by spreading the word on such methods you can reinforce your security posture. To learn more about how we infuse Cyber Threat Intelligence into our Cyber Risk Quantification engine, don’t miss a chance to talk with one of our experts by booking a demo.

