Europe’s 2022 Energy Sector: the Cyber Threats landscape
Citalid - Cyber Risk Quantification, 5 April 2023
This report is a joint CITALID and Sekoia.io analysis pertaining to cyber activities targeting the energy sector in 2022 in Europe. It is based on open sources reports and includes both our investigations and analysis. Information cut-off date is 22 February 2023.
- The energy sector faces multiple risks, including in cyberspace, being an attractive target for multiple threat actors. Possible risks posed by cyber threats notably include cascading effects on the physical layer, which makes this vertical particularly critical.
- The Russo-Ukrainian conflict and its implication for the energy supply worldwide impacted cyber malicious activities targeting the energy vertical, notably originating from State-nexus threats as well as hacktivists groups.
- Cyberespionage campaigns originating from Russia and Ukraine targeting energy-related entities were increasingly observed and / or reported, notably driven by strategic intelligence collection.
- Russia-nexus intrusion sets were observed resuming destructive and disruptive cyber campaigns targeting the energy vertical.
- China-affiliated intrusion sets continued targeting energy entities, notably entities operating in the South China Sea, including involved European stakeholders.
- Lucrative-oriented cybercrime groups and other dark web threat actors continued carrying out campaigns impacting the energy sector during 2022. The slight increase in number of attacks highly likely mirrors the natural growth of the cybercrime threat in recent years.
The energy sector context in 2022
The energy sector remains particularly vulnerable to cyber threats, notably due to two identified structural risks being the complexity of information systems implemented in this sector, including Information Technology (IT) and Operational Technology (OT) networks and solutions, in a context of digitization of activities and IT/OT convergence, as well as third party risk, both increasing the exposure to threat, with possible effects on the physical layer.
In 2022, the energy sector was at the heart of concern in Europe, notably in the light of the Russo-Ukrainian conflict. In this context the energy vertical was targeted by multiple offensive cyber enabled operations, including espionage, disruption, sabotage and information operations. Of particular interest, hacktivist threats, although less advanced, demonstrated a growing interest in disruption operations, notably impacting the energy vertical.
The European energy sector also faced lucrative-oriented cyber malicious campaigns, mostly double extortion attacks operated by Ransomware-as-a-Service (RaaS) groups, and hack-and-leak operations.
Cyberespionage activities continuously support State-aligned strategic interests
Energy is a subject matter and vertical of interest for cyberespionage activities, notably pertaining to strategic data collection and industrial espionage.
Between December 2021 and March 2022, Dragonfly (aka BROMINE), a Russia-nexus intrusion set was observed exfiltrating data from a nuclear safety organisation. Interest for nuclear energy-related entities was also demonstrated on the physical layer, as Russian troops seized the decommissioned Chernobyl nuclear power plant and the Zaporizhzhia Nuclear Power plant. It continued through the conflict, as Calisto notably targeted three nuclear research laboratories in the U.S. in a credential stealing campaign in August and September 2022. Google TAG researchers link this activity to the visit of United Nations inspectors to Ukraine’s Zaporizhzhia nuclear power plant in Russian-controlled territory. Additional Russia-nexus cyberespionage activities include EMBER BEAR (aka SAINT BEAR) targeting personnel involved in Ukrainian energy, Sandworm targeting an energy provider in Ukraine in March 2022, and Gamaredon observed unsuccessfully targeting a NATO refining company later this year. Aligned with Russian activities, the Belarus-nexus intrusion set UNC1151 targeted multiple Ukrainian government websites including those of energy ministries. In parallel, Ukraine-nexus intrusion set Cloud Atlas was reported targeting the Russian energy sector since at least December 2021. Since June 2022, multiple persistent campaigns focused on the energy sector in Belarus and in Russia were observed.
Throughout 2022, China-nexus intrusion sets continued targeting the energy vertical globally. Between November 2021 and April 2022, APT31 was observed targeting the Russian energy sector. This activity is congruent within the timeframe of ongoing negotiations between Russia and China to increase their energy alliance, notably through a new gas pipeline, as well as China’s considerations to increase their investment in Russian energy companies to secure Beijing’s energy supply, and allow Russia to mitigate the impact from lower energy sales to Europe. China-nexus intrusion sets also targeted European companies involved in the South China Sea region energy projects. This included APT40’s targeting of the German company Skyborn Renewables GmbH. during the ScanBox campaign carried out between April 2022 and June 2022, and Mustang Panda targeting a Swiss organisation in the energy and engineering sector in September 2022. Of note, the South China Sea is not only a site for oil and gas exploitation, it is also a critical logistics route for oil and natural gas imports, transporting energy resources through strategic choke points, such as the Strait of Malacca. Switzerland appears to be a country of particular interest for Chinese renewable energy investments, and supplies. The PRC also started prioritising green energy opportunities through the Green Silk Road project since 2021, as part of its own goal of reaching carbon neutrality by 2060 and to display a good record in the frame of UN’s 2030 Agenda for Sustainable Development Goals. We assess that China’s decarbonization strategy is almost certainly already a driver for cyberespionage campaigns originating from China. Of note, China continuously demonstrated its interest in the energy vertical, including nuclear energy, an interest recently renewed in the Global Security Initiative. Energy targeting by China-nexus will almost certainly continue at a global scale in the short to medium term. It is plausible these campaigns notably pertain to intellectual property theft.
In 2022, Iran-nexus intrusion sets, including Lyceum, UNC3890, and MuddyWater were observed continuing targeting the energy sector, notably in Italy, and Russia. We assess that the Russo-Ukrainian conflict was another driver for Teheran’s targeting of the energy vertical in 2022, notably to keep pace with the shift the conflict represented for the global energy market. Of note, in October 2022, Russia and Iran signed a memorandum of understanding for energy cooperation, specifically an oil-gas swap. However energy-related entities based in Israel and Saudi Arabia consistently remain primary targets of Iranian cyberespionage activities. Additionally, we assess the maritime dispute between Israel and Lebanon, notably pertaining to the Karish gas field, as well as gas pipeline discussions between Israel and Turkey are likely to be drivers for continuous Iran-nexus regional cyberespionage activities targeting energy-related organisations and individuals, possibly including involved European stakeholders.
Additional State-nexus cyberespionage campaigns targeting the energy vertical include North Korea-nexus Kimsuky, Lazarus, and Andariel intrusion sets. The latter was reported targeting an unidentified engineering firm involved in the energy and military sectors, as well as energy providers in Canada, Japan, and the United States between February and July 2022.
Sabotage activities highly shaped by the Russo-Ukrainian conflict
As energy was a topic of particular tension between European countries and the Russian Federation, cybersecurity researchers expected the vertical to be a target of interest for destructive cyber operations targeting European and Ukrainian entities originating from Russia, along the same lines as cyber campaigns supporting the annexation of Crimea in 2014. As reported by MSTIC, Russia-nexus intrusion sets’ campaigns targeting the Ukrainian energy sector and nuclear-related entities accounted for respectively 8% and 3% of Russia originating State-nexus activities in 2022. While this represents a significant part of critical infrastructures targeting, Sekoia.io, CITALID and fellow cyber researchers expected even more reported activities. We assess that energy being a possible leverage in the Euro-Russian relationship, this vertical was plausibly part of Russia-nexus intrusion sets’ remits. In April 2022, ESET reported on a malicious cyber campaign by Sandworm targeting an unnamed Ukrainian energy provider’s electrical substation, with the malware Industroyer2, a variant of the Industroyer malware used against Ukraine by the same intrusion set in 2017. In addition to Industroyer2, this intrusion set leveraged destructive malware families. Based on CERT-UA information, the attack was thwarted. In March 2022, a malicious cyber campaign against the Viasat KA-SAT network, attributed to Russia by the UK and U.S. governments notably impacted the operations of 5,800 wind turbines in central Europe. To date, this is the only occurrence of a cyber operation targeting Ukraine with assessed cascading disruptive effects. We assess it is almost certain that physical access to energy-related infrastructures by Russian forces in Ukraine notably contributed to a lesser reliance on cyber means. Of note, to the best of our knowledge, and as the extent of the operational impact of cyber campaigns is difficult to assess, the most impactful attacks against Ukraine’s energy-related entities and infrastructures originating from Russia in the context of the Russo-Ukrainian conflict were kinetic (i.e., missile strikes).
Other observed activities include public declarations warning against reconnaissance efforts, allegedly conducted for follow-up destructive attacks, such as the FBI notice reporting on scanning activities against five U.S. energy companies originating from Russia. Of note, and to the best of our knowledge, there is no indication of targeted destructive campaigns against U.S. energy-related entities previously carried out by Russia-nexus intrusion sets. In April 2022, U.S. CISA released an advisory to warn against existing offensive capabilities specifically designed to target Industrial Automation and Control Systems called PIPEDREAM (aka INCONTROLLER). While no activity leveraging PIPEDREAM was neither reported in open sources at the time of writing, nor officially associated to a specific nexus or intrusion set, this toolset is consistent and congruent with past Russia-associated IACS-related malware. Of particular concern is the apparent focus of scanning activities targeting the Netherlands, including XENOTIME and KAMACITE scanning activities targeting Netherlands-based LNG terminals In November 2022, and the more recent identification of a Russian ship, suspected of mapping the Dutch wind parks in the North Sea by the MIVD, the Dutch military intelligence agency. While we assess it is unlikely Russia will proactively target NATO energy infrastructures in sabotage campaigns, it is plausible these activities pertain to the operational preparedness environment in a context of escalation that would transpire in cyberspace.
State-nexus activities targeting the energy vertical in 2022

Figure 1. State-nexus activities targeting the energy vertical in 2022.
Rise in disruption campaigns indicate an increased structuration of hacktivist groups
The energy industry faced a significant increase in operations conducted by self-claimed hacktivists groups. This activity is deeply circumstantial and mainly fueled by the outbreak of the Russia-Ukraine conflict. For the most part, these hacktivist campaigns consisted in DDoS (Distributed Denial of Service), data disclosure operations, and defacement. Significant incidents included the data disclosure of emails from MashOil and oil pipeline company Transneft, and from Gazprom Linde Engineering joint venture, both claimed by the Anonymous nebula. In August, pro-Russia self-claimed hacktivist group, People’s Cyber Army conducted DDoS campaigns against State-owned Ukrainian nuclear operator Energoatom. In October, another pro-Russia hacktivist group, Xaknet, claimed they conducted a DDoS attack against Ukraine’s high-voltage transmission lines operator Ukrenergo.
As of the date of writing, the energy industry continues to be actively targeted. In February 2023, Anonymous Italia claimed a DDoS against the Russian gas company Norilsk gazprom and electricity company Arktik Energo. Since February 2023, pro-Russia self-claimed hacktivist group NoName057(16) carried out nationwide DDoS campaigns targeting energy operators including pipeline operators, power plants, refineries and distributors in Poland, Slovakia, Lithuania, Estonia, Italy and the United-Kingdom. Observed impacts were generally low and limited to nuisances.
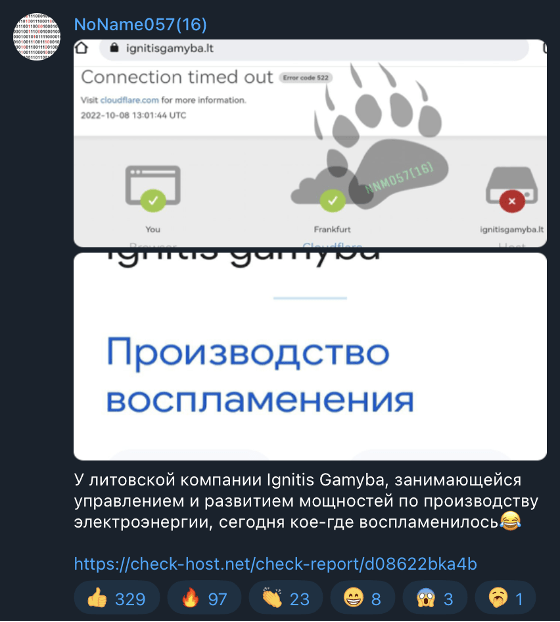
oName057(16)’s DDoS claim against Lithuanian energy company Ignitis Gamyba. SEKOIA.IO Figure 2. NoName057(16)’s DDoS claim against Lithuanian energy company Ignitis Gamyba
Hacktivists’ active targeting of the energy sector is essentially aimed at undermining public’s trust in government and companies’ capacity to protect critical systems and ultimately erode public support for the belligerents through the media coverage of their activity. None of these campaigns aimed at durably disrupting the targeted organisations but rather at maximising the volume of impacted targets. Thus, self-claimed hacktivist intrusion sets essentially focus on highly symbolic and critical sectors such as government, energy, defence and telecommunications. Ideology driven operations against the energy industry were also encouraged and facilitated through the involvement and instrumentalization of hacktivist resources by belligerent States. The creation of the IT army of Ukraine as announced by Vice Prime Minister Mykhailo Fedorov on 26 February 2022 institutionalised this dynamic early in the conflict.
In January 2023, the IT Army of Ukraine claimed to have access to information belonging to the Russian gas company Gazprom. This claim occured a few months after the Main Directorate of Intelligence at the Ministry of Defense of Ukraine (GURMO) conducted cyber operations against Gazprom. In September 2022, Mandiant assessed that pro-Russia self-claimed hacktivists groups including Xaknet, Infoccentr and CyberArmyofRussia_Reborn coordinated data disclosure operations with intrusion sets associated with the Russia Main Intelligence Directorate (GRU). While the precise nature and scale of this coordination remains uncertain (from information sharing to possibly false flag operations), we assess it is almost certain the purpose is to enable higher scale operations to portray civil engagement to the conflict and generate spontaneous, active, and profound support.
Throughout 2022, hacktivists groups were also notably observed increasingly interested in targeting Operational Technology (OT) to conduct disruptive activities, which represents a noticeable shift in these groups’ activities. Hacken.io, a contributor of the IT Army of Ukraine advertised being interested in submission of vulnerabilities notably pertaining to Russian ICS, energy, oil and gas sectors, as part of their initial offensive cyber program. Further examples include the claimed compromise of the Russian oil distribution company Severnaya’s OT systems by NB65, a member of the Anonymous nebula, in February 2022. The same intrusion set encrypted Gazregion’s systems in April 2022 and claimed the compromise of several OpenSCADA devices. In July 2022, Team OneFist, a self-claimed hacktivist group supporting Ukraine, claimed to have compromised several Russian cities electrical control systems and to have deleted data on targeted devices. In August, the same intrusion set also claimed to have conducted a campaign targeting 39 transformer data collectors across Russia and against the Khanty-Mansiysk city natural gas system.
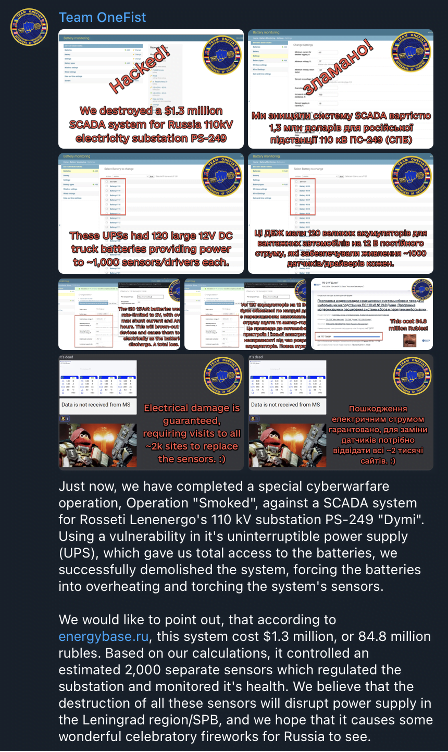
Team OneFist’s Operation “Smoke” against a PS-249 substation. SEKOIA.IO Figure 3. Team OneFist’s Operation “Smoke” against a PS-249 substation
Related TTPs analysis show that these campaigns take advantage of poorly secured environments, actively scanning for exposed devices in countries of interest and compromising infrastructures using valid accounts (default or weak credentials), or by exploiting public facing applications. Impacts varied from data destruction to encryption and defacement. This activity sets a precedent for self-claimed hacktivist groups with seemingly higher capabilities who have had the opportunity to develop new tools and to experiment with the compromise of critical infrastructures, in some instances seeking disruptive effects. We assess that this evolution is structural and is likely to have long term effects on the global level of hacktivist threats.
Likewise, several vendors envisioned these dynamics as the beginning of a new era of hacktivism. While Estonia incidents (2007) and the Russia-Georgia conflict (2008) also capitalised on hacktivist resources, this ongoing conflict projected it at a much higher scale. Moving away from the traditional model of unstructured and decentralised collectives, this conflict is witnessing the emergence of hierarchical groups, aligned with political agendas, possibly supported by State-nexus resources, and capable of conducting large-scale coordinated campaigns.
Info ops align on State-nexus agenda
Out of the overwhelming number of information operations surrounding the Russo-Ukrainian conflict, those pertaining to its impact on the energy sector notably included claims that the rise in energy prices following the conflict in Ukraine is a result of the ‘Great Reset’. European countries were particularly targeted by disinformation claiming that civil society would encounter energy shortage susceptible to political and social unrest. Czechia and Germany were notably targeted by info ops originating from China, as well as originating from Russia. Of note, it is highly likely these two European countries would be primary audiences for information operations, as Czechia was 97% reliant of Russian gas, and Germany was 60% dependent on Russian LNG, notably through NordStream. As previously mentioned, we observed hacktivist groups increasingly claiming access and / or disruption of OT assets, notably in the energy vertical. In June 2022, the pro-Palestinian hacktivist group GhostSec shared video evidence of an exposed interface of ELNet, an energy meter and electrical power meter at Israel-based MATAM high tech park being accessed by the group. According to the group, they gained access to five similar IoT devices in different locations and modified the settings to switch the lights off in all five of them. In September 2022, the same group claimed to have access to Israeli-based Berghof PLC devices. However, investigations by OT cybersecurity researchers at OTORIO indicate that GhostSec almost certainly does not have ICS-related capabilities. We assess this activity is almost certainly part of info ops efforts.
Cybercriminal opportunistic campaigns continue to impact the energy vertical
Over the past year, we identified 34 instances of ransomware groups engaging in malicious campaigns on the energy sector in Europe, compared to 30 known attacks in 2021. This includes data collected from dark web ransomware extortion sites and open source data. The observed incidents notably involved activities pertaining to the electricity supply and distribution, electricity generation and distribution, professional services specialised in the energy sector, storage and transport of energy products, oil and gas services, logistics services to the oil industry, and renewable energy solutions.
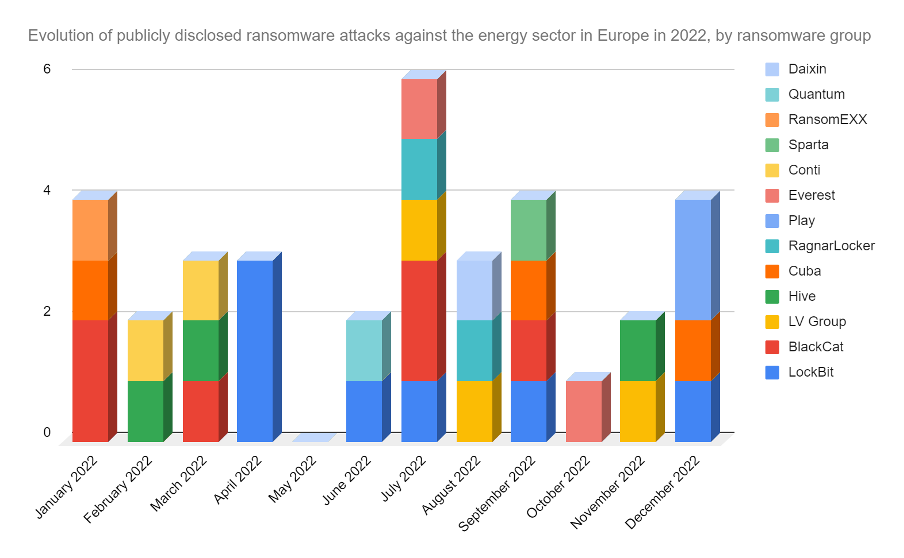
Ransomware activities impacting the energy sector in 2022. Source: SEKOIA.IO Figure 4. Ransomware activities impacting the energy sector in 2022.
The energy sector is exposed to the increasing trend of multiple extortion ransomware attacks. Impacts on these environments, such as encryption, can affect the continuity of critical operations on a national level and have widespread consequences on large communities. Also, data exfiltration can lead to the collection, selling and exploitation of sensitive data such as intellectual property. We add to that financial and reputational damage.
Almost all the observed cases involved the use of data exfiltration and double extortion technique, resulting in follow-up campaigns and contributing to hinder monitoring efforts by the cybersecurity community.
Based on our observations, groups including LockBit, BlackCat, RagnarLocker, Cuba and Hive were the most active collectives carrying out ransomware campaigns impacting the energy sector. Most of these groups operate under the Ransomware-as-a-Service (RaaS) model in lucrative campaigns. We observed the BlackCat ransomware group, composed of Russian speaking affiliates, claiming an increasing number of ransomware attacks targeting critical energy infrastructures in Western Europe in 2022. The group’s victimology notably includes the Italian oil company Eni and the electricity and natural gas supplier Creos Luxembourg SA. BlackCat also claimed responsibility for the campaigns against the German oil and gas storage company Oiltanking and the oil trading firm Mabanaft. Of note, while the timing was congruent, there is no evidence of a link between the BlackCat ransomware attacks and the Russo-Ukrainian conflict, and the events are to be considered as circumstantial. Based on victims’ public statements, the reported damages were minor and did not impact their operational flows.
We assess that ransomware activities affecting the energy sector are still opportunistic by nature. Of note, it is highly likely ransomware threat actors rely on the criticality of energy-related activities to ensure their ransom demands are met, and even request a higher ransom. We assess the energy sector will remain a prime target for highly organised cybercrime actors including ransomware groups.
Based on open source reports, stolen credentials are the most used initial intrusion vectors to conduct ransomware attacks and data breaches. We observe remote access for multiple companies in the energy sector are commonly sold on cybercrime forums and marketplaces. Veracity of these statements must be ensured, as data accuracy might be compromised on the cybercrime platforms, and energy actors need to monitor it closely to detect early evidence of intrusions.
Sale of a remote access to a Spanish energy company on XSS forum. SEKOIA.IO
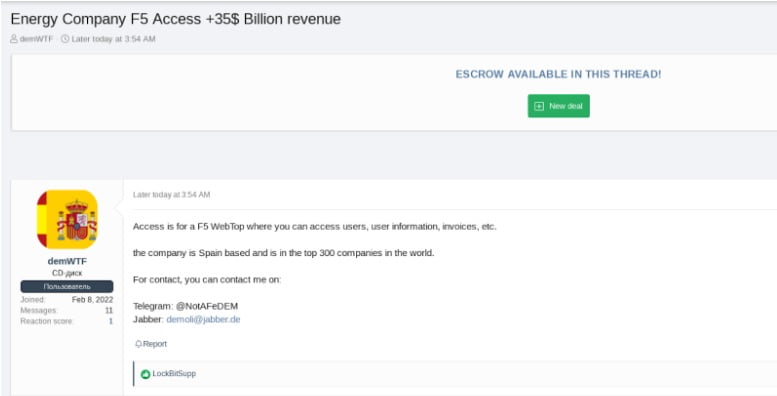
Figure 5. Sale of a remote access to a Spanish energy company on XSS forum
Conclusion
The energy sector’s risk exposure to cyber threats is structural and mostly due to its criticality. Identified risks notably include third party risk and the OT/IT convergence. Additionally it is particularly susceptible to be impacted by geopolitical dynamics.
We assess cyber malicious campaigns including cyberespionage, disruptive, lucrative and destructive activities impacting the energy vertical will continue in the short term.
We further assess the ongoing Russo-Ukrainian conflict will almost certainly continue to be a strong driver for offensive cyber activities in the short term, notably for State-nexus and hacktivists intrusion sets.
Hacktivists are likely to continue their ongoing structuring. Support garnered by these intrusion sets by civil society and possibly State-related entities, as well as the increasing level of advancement of their capabilities will possibly durably impact the cyber threat landscape in the short term.
We also expect to continue observing cyber activities targeting the energy sector originating from China-nexus intrusion sets, notably for industrial espionage and intellectual property theft, highly likely targeting European entities involved.
It is our assessment that while still highly opportunistic, cybercriminal activities will continue impacting the energy vertical, notably through ransomware and hack-and-leak operations.
